Difference between revisions of "HTTPS Provisioning"
Kevin Wilkie (Talk | contribs) |
Kevin Wilkie (Talk | contribs) |
||
| Line 11: | Line 11: | ||
All keystore management is performed using the java /opt/java/bin/keytool command. | All keystore management is performed using the java /opt/java/bin/keytool command. | ||
| − | + | Change into the folder with the keystore | |
cd /opt/ros/resources/prepos/ | cd /opt/ros/resources/prepos/ | ||
| − | |||
| + | Generate a private key | ||
| + | keytool -genkey -alias tomcat -keyalg RSA -keystore roskeystore_new.jks -storepass password -dname "...." | ||
| − | + | Generate a CSR | |
| − | + | keytool -certreq -keyalg RSA -alias tomcat -file certreq.csr -keystore roskeystore_new.jks -storepass password | |
| + | |||
| + | Import certificate into keystore | ||
| + | keytool -import -alias tomcat -keyalg RSA -keystore roskeystore_new.jks -trustcacerts -file certnew.cer -storepass password | ||
| + | |||
| + | |||
| + | '''Optional''' | ||
| + | Generating a new keystore and self signed cert in /opt/ros/resources/prepos/roskeystore_new.jks | ||
| + | cd /opt/ros/resources/prepos/ | ||
| + | keytool -genkey -keyalg RSA -alias selfsigned -keystore roskeystore_new.jks -storepass password -validity 360 -keysize 2048 | ||
Removing an unrequired certificate | Removing an unrequired certificate | ||
keytool -delete -alias cashelros -keystore roskeystore_kw.jks | keytool -delete -alias cashelros -keystore roskeystore_kw.jks | ||
Revision as of 08:30, 24 October 2016
You can view and change which ketstore is in use for SSL in the SSL panel of the Settings page
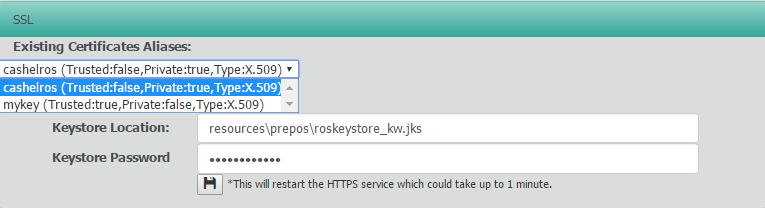
Here you can use the drop down to view the certificates in the current keystore.
We highly recommend you use a different keystore name as future updates may overwrite the existing file.
In this example, we've copied the origional keystore (/opt/ros/resources/prepos/roskeystore.jks to /opt/ros/resources/prepos/roskeystore_new.jks) We've kept the same default keystore password "cashelros254"
All keystore management is performed using the java /opt/java/bin/keytool command.
Change into the folder with the keystore
cd /opt/ros/resources/prepos/
Generate a private key
keytool -genkey -alias tomcat -keyalg RSA -keystore roskeystore_new.jks -storepass password -dname "...."
Generate a CSR
keytool -certreq -keyalg RSA -alias tomcat -file certreq.csr -keystore roskeystore_new.jks -storepass password
Import certificate into keystore
keytool -import -alias tomcat -keyalg RSA -keystore roskeystore_new.jks -trustcacerts -file certnew.cer -storepass password
Optional
Generating a new keystore and self signed cert in /opt/ros/resources/prepos/roskeystore_new.jks
cd /opt/ros/resources/prepos/ keytool -genkey -keyalg RSA -alias selfsigned -keystore roskeystore_new.jks -storepass password -validity 360 -keysize 2048
Removing an unrequired certificate
keytool -delete -alias cashelros -keystore roskeystore_kw.jks