Difference between revisions of "HTTPS Provisioning"
| Line 12: | Line 12: | ||
'''2.''' To set the SAN (Subject Alternative Name) field in the CSR (Certificate Signing Request), create or edit the <strong>.cnf</strong> file as required for the target system. Use the following example to fill the <strong>.cnf</strong> file. | '''2.''' To set the SAN (Subject Alternative Name) field in the CSR (Certificate Signing Request), create or edit the <strong>.cnf</strong> file as required for the target system. Use the following example to fill the <strong>.cnf</strong> file. | ||
| + | {| class="wikitable" | ||
| + | |- | ||
| + | | '''Note:''' You must fill the fields in italic font with company specific information, especially if seen in the certificate creation section on customer side. | ||
| + | |} | ||
[ req ] | [ req ] | ||
| − | default_bits = 2048 | + | default_bits = 2048 ''(option: 4096)'' |
distinguished_name = req_distinguished_name | distinguished_name = req_distinguished_name | ||
req_extensions = req_ext | req_extensions = req_ext | ||
[ req_distinguished_name ] | [ req_distinguished_name ] | ||
| − | countryName = Country Name (2 letter code) | + | countryName = ''Country Name (2 letter code)'' |
| − | stateOrProvinceName = State or Province Name (full name) | + | stateOrProvinceName = ''State or Province Name (full name)'' |
| − | localityName = Locality Name ( | + | localityName = ''Locality Name (for example, city)'' |
| − | organizationName = Organization Name ( | + | organizationName = ''Organization Name (for example, company)'' |
| − | commonName = Common Name ( | + | commonName = ''Common Name (for example, server FQDN or YOUR name)'' |
| − | [ req_ext ] | + | [ req_ext ] |
| − | subjectAltName = @alt_names | + | subjectAltName = @alt_names |
[alt_names] | [alt_names] | ||
| − | DNS.1 = 5l60p12.ds.jdsu.net | + | DNS.1 = '''5l60p12.ds.jdsu.net''' |
DNS.2 = {name without FQDN .com) | DNS.2 = {name without FQDN .com) | ||
DNS.3 = {can use the IP} | DNS.3 = {can use the IP} | ||
Revision as of 08:22, 14 March 2024
SSL certificate generation on GigaFlow
To generate an SSL certificate o GigaFlow, perform the following steps:
1. To change the current directory to the web server one that contains the keystore, on your Linux VM or appliance in the terminal prompt, run the following command:
cd /opt/ros/resources/prepos
Note: You can later make sure that the created files have the same chown/chmod permissions as the previous files, respectively root/root and/or gigaflow/viavi.
|
2. To set the SAN (Subject Alternative Name) field in the CSR (Certificate Signing Request), create or edit the .cnf file as required for the target system. Use the following example to fill the .cnf file.
| Note: You must fill the fields in italic font with company specific information, especially if seen in the certificate creation section on customer side. |
[ req ]
default_bits = 2048 (option: 4096)
distinguished_name = req_distinguished_name
req_extensions = req_ext
[ req_distinguished_name ]
countryName = Country Name (2 letter code)
stateOrProvinceName = State or Province Name (full name)
localityName = Locality Name (for example, city)
organizationName = Organization Name (for example, company)
commonName = Common Name (for example, server FQDN or YOUR name)
[ req_ext ]
subjectAltName = @alt_names
[alt_names]
DNS.1 = 5l60p12.ds.jdsu.net
DNS.2 = {name without FQDN .com)
DNS.3 = {can use the IP}
You can view and change which keystore is in use for SSL in the SSL panel of the Settings page
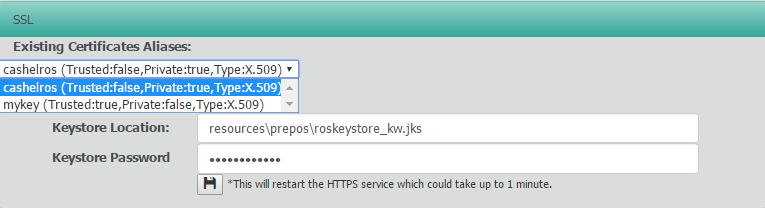
Here you can use the drop down to view the certificates in the current keystore.
We highly recommend you use a different keystore name as future updates may overwrite the existing file.
In this example, we've copied the origional keystore (/opt/ros/resources/prepos/roskeystore.jks to /opt/ros/resources/prepos/roskeystore_new.jks) We've kept the same default keystore password "cashelros254"
All keystore management is performed using the java /opt/java/bin/keytool command.
Change into the folder with the keystore
cd /opt/ros/resources/prepos/
Generate a private key
keytool -genkey -alias tomcat -keyalg RSA -keystore roskeystore_new.jks -storepass password -dname "...."
Generate a CSR
keytool -certreq -keyalg RSA -alias tomcat -file certreq.csr -keystore roskeystore_new.jks -storepass password
Import certificate into keystore
keytool -import -alias tomcat -keyalg RSA -keystore roskeystore_new.jks -trustcacerts -file certnew.cer -storepass password
If you've change the keystore location or password, update anuview Flow to reflect this and restart the service.
Optional Generating a new keystore and self signed cert in /opt/ros/resources/prepos/roskeystore_new.jks
cd /opt/ros/resources/prepos/ keytool -genkey -keyalg RSA -alias selfsigned -keystore roskeystore_new.jks -storepass password -validity 360 -keysize 2048
Removing an unrequired certificate
keytool -delete -alias cashelros -keystore roskeystore_kw.jks
if a certificate is to work in Chorme it must have a SAN entry. This has been a requirement in Chrome for the last 2 years. It does not appear that other browsers have this requirement
Generate Private key
keytool -genkey -alias tomcat -keyalg RSA -keystore roskeystore_new.jks -storepass password -dname "CN=gigaflow.company.net "
Gererate CSR
keytool -certreq -keyalg RSA -alias tomcat -file certreq.csr -keystore roskeystore_new.jks -storepass password -ext SAN=dns:gigaflow,dns:gigaflow.company.net
you can check your csr file to ensre that the san entires are present by
keytool -printcertreq -file certreq.csr -v
For client requests from the server you must add the certs to the JRE ca store. Password is changeit
keytool -import -trustcacerts -file [certificate] -alias [alias] -keystore JAVA_HOME/lib/security/cacerts
If you already have a crt and private key file you can create a new keystore by first creating a pkcs12 file
openssl pkcs12 -export -in [filename-certificate] -inkey [filename-key] -name [host] -out [filename-new-PKCS-12.p12] keytool -importkeystore -deststorepass [password] -destkeystore [filename-new-keystore.jks] -srckeystore [filename-new-PKCS-12.p12] -srcstoretype PKCS12