Difference between revisions of "HTTPS Provisioning"
| (28 intermediate revisions by one user not shown) | |||
| Line 1: | Line 1: | ||
| + | __TOC__ | ||
= SSL certificate generation on GigaFlow = | = SSL certificate generation on GigaFlow = | ||
| − | To generate an SSL certificate | + | To generate an SSL certificate for GigaFlow, perform the following steps: |
| − | + | {| class="wikitable" | |
| − | ''' | + | |- |
| + | | '''Note:''' If you have the possibility to create a private key file and a '''.p12''' or a '''.pfx''' complete certificate with a password (that includes root, intermediate, and server certificates), then you can skip steps 1 to 5 and go directly to step 6. | ||
| + | The private key and the '''.p12''' or '''.pfx''' files can be copied to '''<code>/opt/ros/resources/prepos</code>''' on Linux or to '''<code>C:\GigaFlow\Flow\resources\prepos</code>''' on Windows. | ||
| + | |} | ||
| − | <code>cd /opt/ros/resources/prepos</code> | + | '''1.''' To change the current directory to the web server one, that contains the keystore, perform the following steps: |
| + | *For Linux, on your VM or appliance in the terminal prompt, run the following command: | ||
| + | '''<code>cd /opt/ros/resources/prepos</code>''' | ||
{| class="wikitable" | {| class="wikitable" | ||
|- | |- | ||
| − | | '''Note:''' You can later make sure that the created files have the same chown/chmod permissions as the previous files, respectively '''<code>root/root</code>''' and/or '''<code>gigaflow/viavi</code>'''. | + | | '''Note:''' You can later make sure that the created files have the same '''chown/chmod''' permissions as the previous files, respectively '''<code>root/root</code>''' and/or '''<code>gigaflow/viavi</code>'''. |
|} | |} | ||
| + | *For Windows, change the folder to '''<code>C:\GigaFlow\Flow\resources\prepos</code>'''. | ||
'''2.''' To set the SAN (Subject Alternative Name) field in the CSR (Certificate Signing Request), create or edit the <strong>.cnf</strong> file as required for the target system. Use the following example to fill the <strong>.cnf</strong> file. | '''2.''' To set the SAN (Subject Alternative Name) field in the CSR (Certificate Signing Request), create or edit the <strong>.cnf</strong> file as required for the target system. Use the following example to fill the <strong>.cnf</strong> file. | ||
| Line 33: | Line 40: | ||
<code>DNS.3 = (can use the IP)</code> | <code>DNS.3 = (can use the IP)</code> | ||
| − | '''3.''' To generate the public/private keypair and CSR using <strong>.cnf</strong> file, use the following example: | + | '''3.''' To generate the public/private keypair and CSR using the <strong>.cnf</strong> file, use the following example: |
<code>openssl req -out gigaflow1_20240129.csr -newkey rsa:2048 -nodes -keyout gigaflow1_20240129.key -config gigaflow1.cnf</code> | <code>openssl req -out gigaflow1_20240129.csr -newkey rsa:2048 -nodes -keyout gigaflow1_20240129.key -config gigaflow1.cnf</code> | ||
{| class="wikitable" | {| class="wikitable" | ||
|- | |- | ||
| − | | '''Note:''' The file created with <code>-keyout</code> command, '''*.key''' will be used later. | + | | '''Note:''' The file created with the <code>-keyout</code> command, '''*.key''' will be used later. |
|} | |} | ||
'''4.''' Submit the CSR to the CA (Certificate Authority). The CA will generate the '''cert''' file. | '''4.''' Submit the CSR to the CA (Certificate Authority). The CA will generate the '''cert''' file. | ||
* Collect the '''cert''' file from CA. | * Collect the '''cert''' file from CA. | ||
| − | * If possible get a complete chain from the customer or create a password protected '''P12''' chain from the CA files, the '''cert''' file, and the private key. | + | * If possible, get a complete chain from the customer or create a password protected '''P12''' chain from the CA files, the '''cert''' file, and the private key. |
* If CA provides a '''*.pem''' file that contains all 3 sections, then use that file. | * If CA provides a '''*.pem''' file that contains all 3 sections, then use that file. | ||
* To create a file with separate '''.cer''' files from CA, follow the below example: | * To create a file with separate '''.cer''' files from CA, follow the below example: | ||
<code>cat <signed_cert_filename> <intermediate.cert> [<intermediate2.cert>] > GigaFlow1_20240129_chain.txt{.pem}</code> | <code>cat <signed_cert_filename> <intermediate.cert> [<intermediate2.cert>] > GigaFlow1_20240129_chain.txt{.pem}</code> | ||
| − | '''5''' To create a '''.p12''' certificate used for the server, follow the below example: | + | '''5.''' To create a '''.p12''' certificate used for the server, follow the below example: |
<code>openssl pkcs12 -export -in GigaFlow1_20240129_chain.txt -inkey <private_key_filename> -name ‘GigaFlow1_20240129’ -out GigaFlow1_20240129.p12</code> | <code>openssl pkcs12 -export -in GigaFlow1_20240129_chain.txt -inkey <private_key_filename> -name ‘GigaFlow1_20240129’ -out GigaFlow1_20240129.p12</code> | ||
| Line 55: | Line 62: | ||
<br />'''name''' - use the DNS name of the server. | <br />'''name''' - use the DNS name of the server. | ||
<br />'''out''' - the name of the files to be used by GigaFlow ('''.p12'''). | <br />'''out''' - the name of the files to be used by GigaFlow ('''.p12'''). | ||
| + | <br />Example: | ||
| + | <br />[[File:Sample_command_and_output.png]] | ||
| + | '''6.''' In the GigaFlow UI, under '''System''' > '''Global''' > '''SSL''', select the newly created '''.p12''' files. | ||
| + | {| class="wikitable" | ||
| + | |- | ||
| + | | '''Note:''' If the certificate is valid, then '''https''' shows again and the '''SSL''' page shows the certificate alias(es). This way your GigaFlow '''https''' connection is now secured. | ||
| + | |} | ||
| + | {| class="wikitable" | ||
| + | |- | ||
| + | |'''Note:''' If the certificate is invalid or the file change does not work, then the '''https''' connection is refused and the GigaFlow UI will freeze. | ||
| + | In this case use an '''http''' connection to change the '''Keystore Location''' back to '''<code>resources\prepos\roskeystore.jks</code>''' and enter as '''Keystore Password''' the string '''cashelros254'''. | ||
| + | A new certificate needs to be created and tested. | ||
| + | |} | ||
| + | '''a.''' To register the new certificate connect using '''http''' to port <code>7902</code> or at appliance Web UI, since next step can disconnect the '''https''' connection. | ||
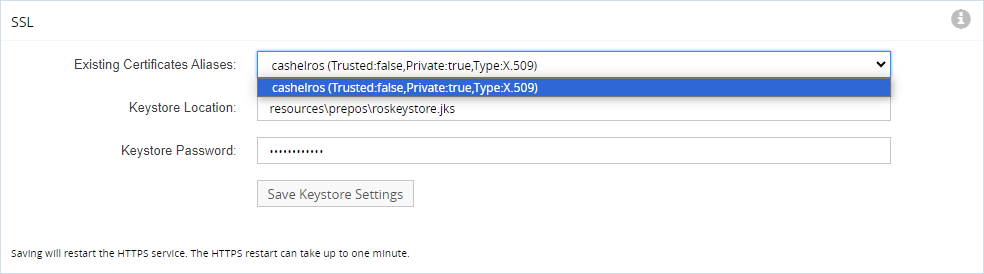
| + | '''b.''' In the '''Keystore Location''' field enter the name of new certificate that needs to be present in the '''prepos''' directory. | ||
| − | + | <br />[[File:ssl_certificates.png]] | |
| + | '''c.''' In the '''Keystore Password''' enter the matching password (no password will not work). | ||
| + | {| class="wikitable" | ||
| + | |- | ||
| + | | '''Note:''' GigaFlow will auto-restart the '''https''' listener to immediately use the new certificate. You are not required to manually restart the server and/or the service. | ||
| + | |} | ||
| − | + | {| class="wikitable" | |
| − | + | |- | |
| − | + | | '''Note:''' The method used here may depend on the format in which the certificate(s) is/are provided by the CA. | |
| − | + | |} | |
| − | + | '''d.''' Install the '''P12''' into the following folders: | |
| − | + | * For Linux: '''<code>/opt/ros/resources/prepos</code>''' on the GigaFlow server. | |
| − | + | * For Windows: '''<code>C:\GigaFlow\Flow\resources\prepos</code>''' on the GigaFlow server. | |
| − | + | '''e.''' Adjust the file '''chmod/chown''' attributes on the '''P12''' to match the previous '''.p12''' file. | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | ''' | + | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
Latest revision as of 20:14, 19 March 2024
Contents |
SSL certificate generation on GigaFlow
To generate an SSL certificate for GigaFlow, perform the following steps:
| Note: If you have the possibility to create a private key file and a .p12 or a .pfx complete certificate with a password (that includes root, intermediate, and server certificates), then you can skip steps 1 to 5 and go directly to step 6.
The private key and the .p12 or .pfx files can be copied to |
1. To change the current directory to the web server one, that contains the keystore, perform the following steps:
- For Linux, on your VM or appliance in the terminal prompt, run the following command:
cd /opt/ros/resources/prepos
Note: You can later make sure that the created files have the same chown/chmod permissions as the previous files, respectively root/root and/or gigaflow/viavi.
|
- For Windows, change the folder to
C:\GigaFlow\Flow\resources\prepos.
2. To set the SAN (Subject Alternative Name) field in the CSR (Certificate Signing Request), create or edit the .cnf file as required for the target system. Use the following example to fill the .cnf file.
| Note: You must fill the fields in italic font with company specific information, especially if seen in the certificate creation section on customer side. |
[ req ]default_bits = 2048(another option:4096)distinguished_name = req_distinguished_namereq_extensions = req_ext[ req_distinguished_name ]countryName =Country Name (2 letter code)stateOrProvinceName =State or Province Name (full name)localityName =Locality Name (for example, city)organizationName =Organization Name (for example, company)commonName =Common Name (for example, server FQDN or YOUR name)[ req_ext ]subjectAltName = @alt_names[alt_names]DNS.1 = 5l60p12.ds.jdsu.netDNS.2 = (name without FQDN .com)DNS.3 = (can use the IP)
3. To generate the public/private keypair and CSR using the .cnf file, use the following example:
openssl req -out gigaflow1_20240129.csr -newkey rsa:2048 -nodes -keyout gigaflow1_20240129.key -config gigaflow1.cnf
Note: The file created with the -keyout command, *.key will be used later.
|
4. Submit the CSR to the CA (Certificate Authority). The CA will generate the cert file.
- Collect the cert file from CA.
- If possible, get a complete chain from the customer or create a password protected P12 chain from the CA files, the cert file, and the private key.
- If CA provides a *.pem file that contains all 3 sections, then use that file.
- To create a file with separate .cer files from CA, follow the below example:
cat <signed_cert_filename> <intermediate.cert> [<intermediate2.cert>] > GigaFlow1_20240129_chain.txt{.pem}
5. To create a .p12 certificate used for the server, follow the below example:
openssl pkcs12 -export -in GigaFlow1_20240129_chain.txt -inkey <private_key_filename> -name ‘GigaFlow1_20240129’ -out GigaFlow1_20240129.p12
The command requires the following parameters and will ask (also confirm) for a .p12 password to be created then used later in GigaFlow (no password fails inside GigaFlow):
in - use the certificate from CA .pem or chain of separate .txt files (.pem).
inkey - use the key created above in step 3. (.key).
name - use the DNS name of the server.
out - the name of the files to be used by GigaFlow (.p12).
Example:

6. In the GigaFlow UI, under System > Global > SSL, select the newly created .p12 files.
| Note: If the certificate is valid, then https shows again and the SSL page shows the certificate alias(es). This way your GigaFlow https connection is now secured. |
| Note: If the certificate is invalid or the file change does not work, then the https connection is refused and the GigaFlow UI will freeze.
In this case use an http connection to change the Keystore Location back to |
a. To register the new certificate connect using http to port 7902 or at appliance Web UI, since next step can disconnect the https connection.
b. In the Keystore Location field enter the name of new certificate that needs to be present in the prepos directory.
c. In the Keystore Password enter the matching password (no password will not work).
| Note: GigaFlow will auto-restart the https listener to immediately use the new certificate. You are not required to manually restart the server and/or the service. |
| Note: The method used here may depend on the format in which the certificate(s) is/are provided by the CA. |
d. Install the P12 into the following folders:
- For Linux:
/opt/ros/resources/preposon the GigaFlow server. - For Windows:
C:\GigaFlow\Flow\resources\preposon the GigaFlow server.
e. Adjust the file chmod/chown attributes on the P12 to match the previous .p12 file.